By default, Windows hides standard file types. For example, SecureFile.exe will show as SecureFile in explorer or on your desktop, PersonalImage.png will show as PersonalImage, and so forth. If malware names itself PersonalImage.png.exe, what do you think will happen?
Windows will only show you PersonalImage.png. But when you try to open this “image”, malware will start and run on your machine. Therefore, it would be best if you showed hidden file extensions to mitigate this potential problem.
See: https://support.microsoft.com/en-us/windows/common-file-name-extensions-in-windows-da4a4430-8e76-89c5-59f7-1cdbbc75cb01
PPL is a security feature designed to protect high-value processes from tampering—even by other processes running as SYSTEM. When a process like LSASS is run as a PPL, access to its memory space is heavily restricted. Only trusted, Microsoft-signed binaries with specific protection levels can read or write to it.
PPL uses different protection levels, and LSASS typically runs as PsProtectedSignerLsa-Light. This limits access to processes that either:
This means that even tools running with administrative privileges (like procdump.exe) cannot access LSASS unless they’re properly signed and allowed.
An entry in the registry can also be used to define the LSASS as a PPL, also see at Microsoft Docs
Configuring LSA Protection Mode
RunAsPPL = dword: 1 under HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa setVerifying LSA Protection Mode
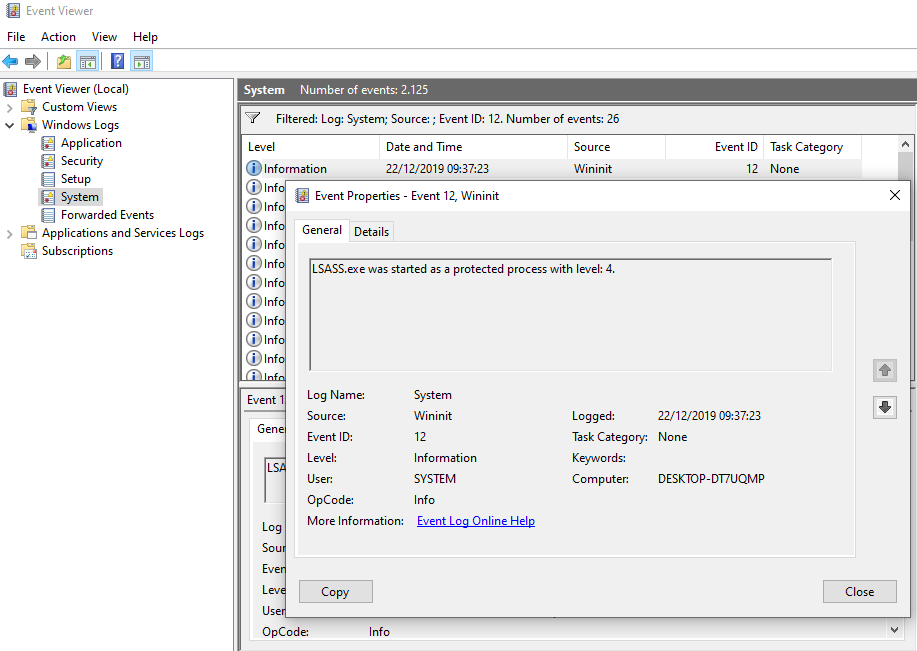
Once the registry key has been set and rebooting has taken place, verification can be performed as follows: The event with the source Wininit and event ID 12 is: LSASS.exe was started as a protected process with level: 4
